CMMC Compliance Service
Comprehensive CMMC Compliance Service
Ensure your organization’s readiness for CMMC certification with Systems Engineering, the trusted partner providing end-to-end compliance services tailored to your maturity stage and requirements. As a leading CMMC Registered Practitioner Organization (RPO) for advisory and managed services for CMMC, we are actively working with many clients in the DIB to ensure they are ready to secure contracts.
We combine managed IT services, deep cybersecurity expertise and capabilities, and a rich pool of highly CMMC-trained teams to guide and help implement all the facets to gain and maintain CMMC compliance.
Trusted by Defense Industrial Base Clients
Systems Engineering already collaborates with numerous organizations in the DIB and defense contractors, equipping them with tailored strategies and technical solutions that align with their specific needs. This extensive experience places us in a unique position to understand the challenges and requirements of organizations on their path to CMMC compliance.
The Path to CMMC Compliance: A Holistic Approach to Accelerate Compliance
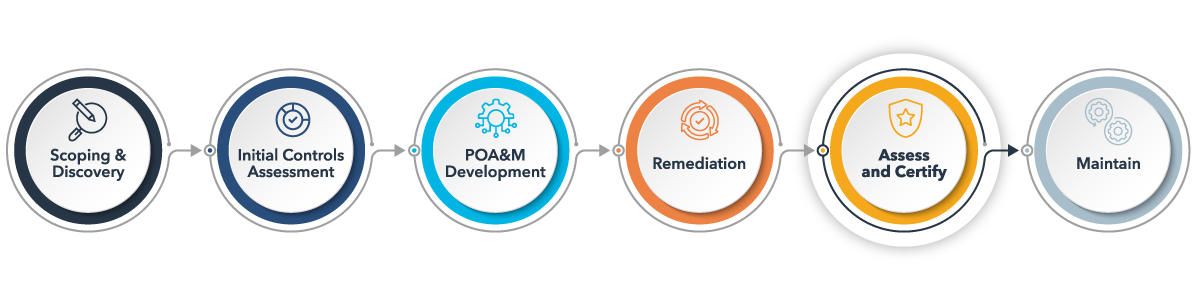
1. Scoping & Discovery
- Inventory Analysis: Comprehensive inventory of applications, vendors, and devices.
- Boundary Identification: Define the scope to identify Controlled Unclassified Information (CUI).
- Data Flow Diagram: Visual representation of CUI movement.
- System Security Plan (SSP) Development. The System Security Plan (SSP) for CMMC is a crucial document that describes an organization’s IT systems, defines the boundaries of its cybersecurity environment, and details the controls and procedures implemented to meet CMMC requirements. It includes a comprehensive inventory of applications, vendors, and devices, with data flow diagrams and boundary identifications to set the groundwork for assessments and remediation.
2. Initial Controls Assessment
- NIST 800-171 Alignment: Review alignment with NIST standards.
- SPRS Scoring: Generate inputs for Supplier Performance Risk System (SPRS) scoring to evaluating your compliance with NIST 800-171 controls, providing a standardized score that reflects the cybersecurity maturity and readiness for CMMC assessments.
3. Plan of Action & Milestones (POA&M) Development
- Task Creation & Responsibility: Assign clear tasks and timelines.
- Strategic Planning: Identify actions and roadmap required for remediation.
4. Remediation
- Policy & Procedure Development: Draft and implement compliance policies.
- Security Enhancements: Execute engineering projects and necessary platform migrations.
- Training: Provide staff training to ensure adherence.
5. Certification Preparation
- Pre-Assessment Checks: Conduct mock assessments to ensure readiness.
- Documentation Review: Verify comprehensive assessment documentation.
6. Ongoing Maintenance
- Continuous Monitoring: Regular updates and advisory support to maintain compliance.
- Adjustments: Adapt to evolving regulatory standards.
The Importance of Mastering the 320 Points of the Assessment
Understanding the 320 assessment points of the CMMC assessment is essential to ensuring your certification success. Each point reflects critical cybersecurity requirements that your organization must meet to maintain compliance. Our detailed approach ensures:
- Thorough Coverage: Systems Engineering’s assessment readiness program meticulously addresses all 320 assessment points, leaving no aspect overlooked.
- Strategic Expertise: Our team provides insights and actionable guidance based on deep knowledge of these requirements.
- Operationally Aligned to NIST: Systems Engineering is one of the only Managed Service Providers to have compliance alignment built into every facet of our operations.
Accelerate Your Path to CMMC Compliance
Secure Enclaves: Charting the Best Course
Secure enclaves are a strategic solution for organizations pursuing CMMC compliance. By isolating CUI and applying robust security controls, enclaves can protect CUI while reducing the scope of systems and personnel subject to compliance requirements. This targeted approach simplifies compliance, enhances security, and streamlines operations allowing your organization to continue working on and win future DoD contracts.
The secure enclave decision needs to be made early in your compliance journey. Explore the pros and cons of secure enclaves and ensure you choose the right path for your organization and its needs.
Expert Support for CMMC Enclave Implementation
If your organization needs an isolated computing environment for storing and processing CUI, our team can design and implement a tailored enclave within Microsoft. With our expertise, we ensure your enclave is built to protect CUI and fully aligns with CMMC requirements.
Is a Secure Enclave Right for Your Organization?
While enclaves provide significant advantages, they are not a one-size-fits-all solution. Poorly designed or unnecessary implementations can lead to operational inefficiencies, increased costs, and compliance gaps. If you’re exploring a CMMC enclave but are unsure if it’s the right solution, our experts will evaluate your organization’s needs and resources to help you determine the best course of action.
Why Partner with a CMMC Registered Practitioner Organization (RPO)?
Collaborating with an RPO like Systems Engineering is fundamental for effective navigation through the complexities of CMMC compliance:
- Expertise Across the Team: Our team includes trained specialists in account management, advisory services, and managed IT support, ensuring comprehensive and seamless service delivery.
- Proven Track Record: We have a robust history of partnering with defense contractors to drive them toward successful CMMC certification.